The internet is vast, complicated, and infinitely interconnected, but our view of its extensive set of interrelated and interconnected risks is narrow and woefully incomplete.
We don’t have enough consistent, high quality data to evaluate the relative effectiveness of cybersecurity mitigation strategies or predict future outcomes, let alone begin to untangle the wider determinants, impacts, or flows of risk.
To meet the evolving cybersecurity threats of tomorrow, we need a change of perspective. We need a wider view and a more rigorous, data-driven approach.
The internet is vast, complicated, and infinitely interconnected, but our view of its extensive set of interrelated and interconnected risks is narrow and woefully incomplete.
We don’t have enough consistent, high quality data to evaluate the relative effectiveness of cybersecurity mitigation strategies or predict future outcomes, let alone begin to untangle the wider determinants, impacts, or flows of risk.
To meet the evolving cybersecurity threats of tomorrow, we need a change of perspective. We need a wider view and a more rigorous, data-driven approach.
The internet is vast, complicated, and infinitely interconnected, but our view of its extensive set of interrelated and interconnected risks is narrow and woefully incomplete.
We don’t have enough consistent, high quality data to evaluate the relative effectiveness of cybersecurity mitigation strategies or predict future outcomes, let alone begin to untangle the wider determinants, impacts, or flows of risk.
To meet the evolving cybersecurity threats of tomorrow, we need a change of perspective. We need a wider view and a more rigorous, data-driven approach.
WE NEED A SCIENCE OF CYBER PUBLIC HEALTH
Medical professionals faced a similar challenge at the dawn of the 19th century as outbreaks of infectious diseases spiked and health disparities between wealthy and poor communities ballooned.
The early pioneers of public health and its diagnostic discipline – epidemiology – shifted the perspective of medicine over the course of the 19th century, effectively revolutionizing the treatment and mitigation of infectious diseases and beyond.
The core components of this new shift in perspective were:
WE NEED A SCIENCE OF CYBER PUBLIC HEALTH
Medical professionals faced a similar challenge at the dawn of the 19th century as outbreaks of infectious diseases spiked and health disparities between wealthy and poor communities ballooned.
The early pioneers of public health and its diagnostic discipline – epidemiology – shifted the perspective of medicine over the course of the 19th century, effectively revolutionizing the treatment and mitigation of infectious diseases and beyond.
The core components of this new shift in perspective were:
WE NEED A SCIENCE OF CYBER PUBLIC HEALTH
Medical professionals faced a similar challenge at the dawn of the 19th century as outbreaks of infectious diseases spiked and health disparities between wealthy and poor communities ballooned.
The early pioneers of public health and its diagnostic discipline, epidemiology, shifted the perspective of medicine over the course of the 19th century, effectively revolutionizing the treatment and mitigation of infectious diseases and beyond.
The core components of this new shift in perspective were:
DATA-DRIVEN SCIENTIFIC
INVESTIGATION
The adoption of data-driven scientific investigation techniques exposed flaws in the empirical foundations of existing medical knowledge and common treatments that proved to be either ineffective or harmful.
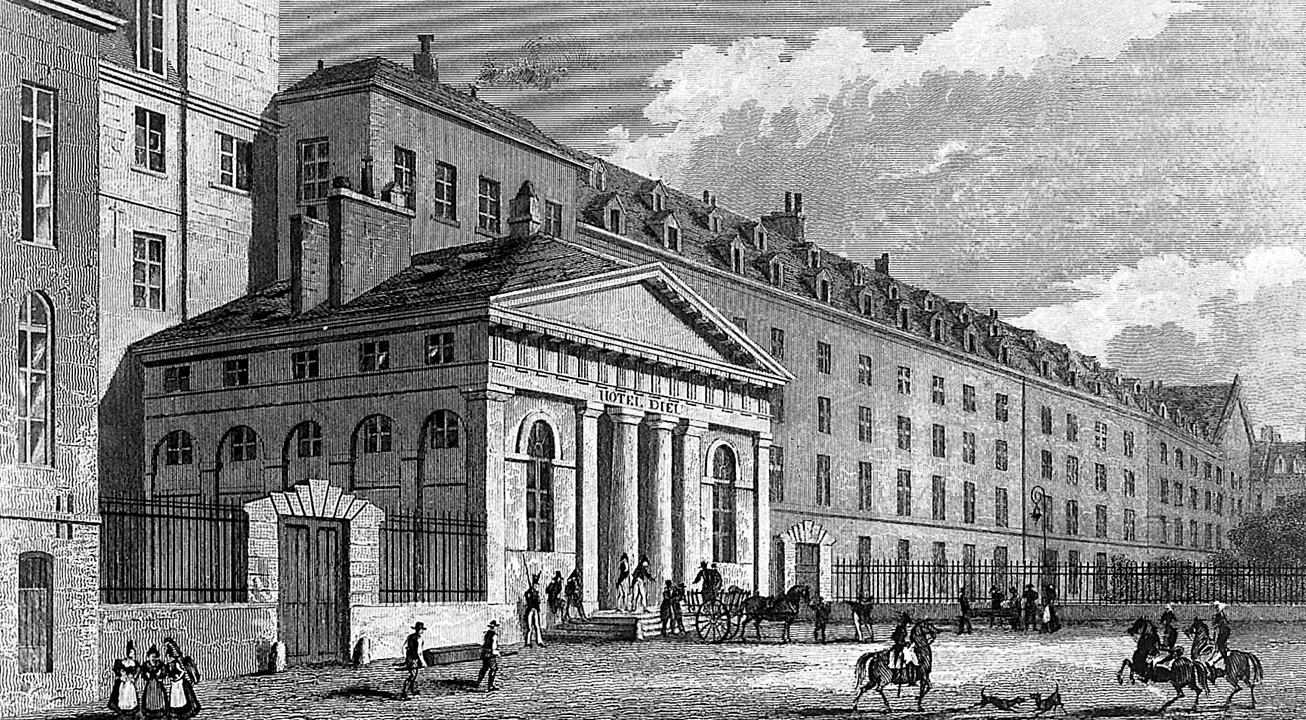
DATA-DRIVEN SCIENTIFIC
INVESTIGATION
Embracing data-driven, scientific investigation techniques exposed flaws in the empirical foundations of existing medical knowledge and common treatments that were either ineffective or harmful.
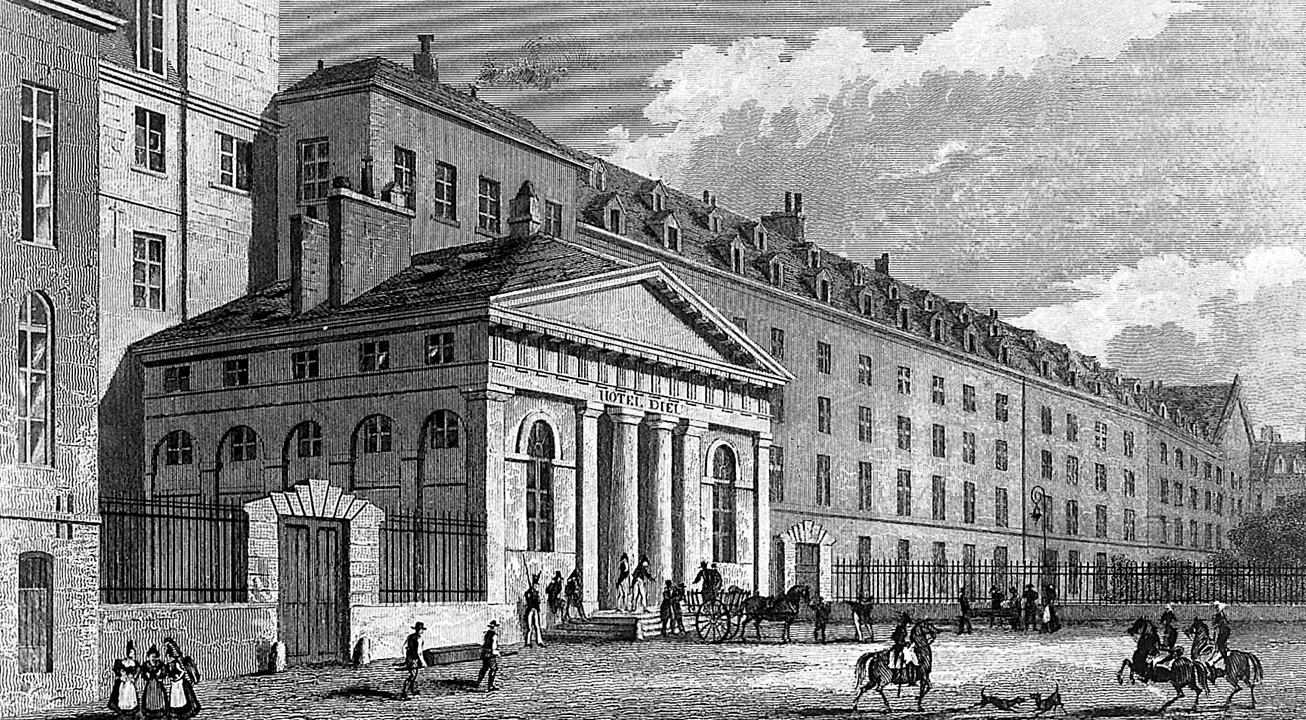
DATA-DRIVEN SCIENTIFIC
INVESTIGATION
The adoption of data-driven scientific investigation techniques exposed flaws in the empirical foundations of existing medical knowledge and common treatments that proved to be either ineffective or harmful.
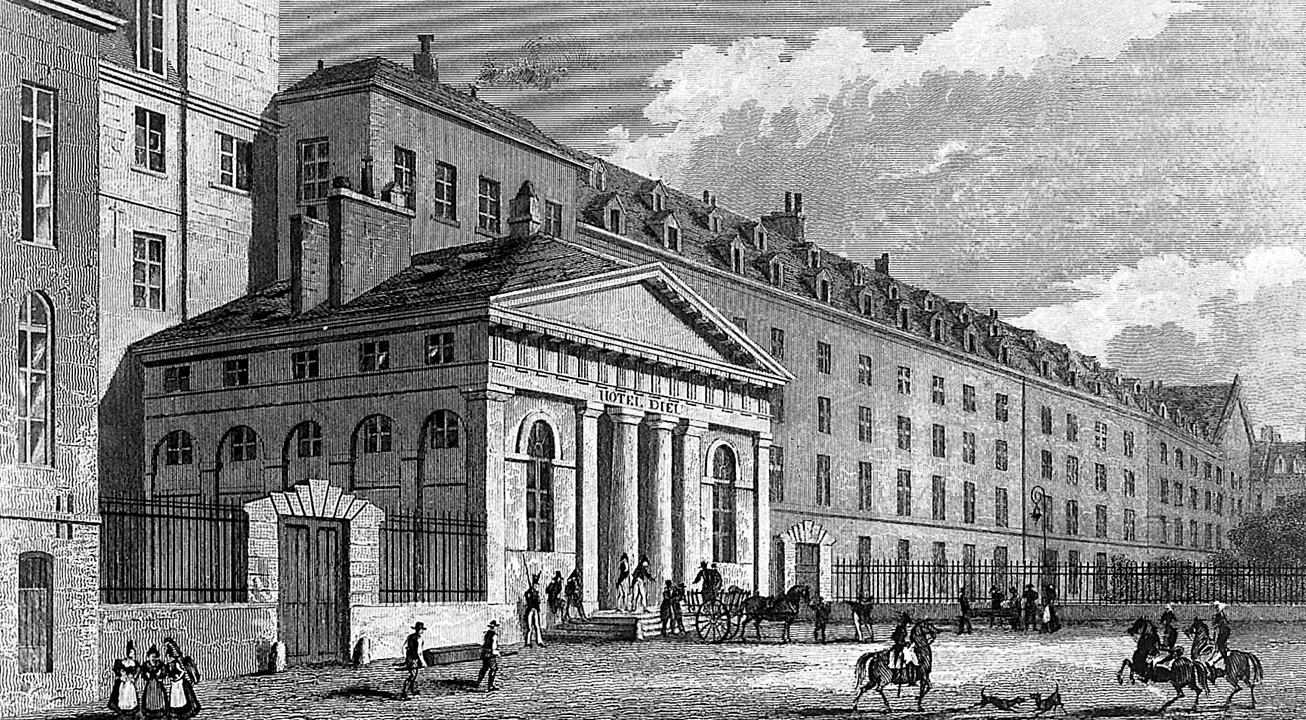
Using clinical records to test treatments
The proliferation of public hospitals created the first significant collections of clinical records. French doctor Pierre Charles Alexandre Louis used early statistical analysis techniques to discredit the use of leeches in bloodletting in 1828, and many credit his approach as inspiration for modern evidence-based medicine techniques including clinical trials and differential diagnosis techniques.
Using clinical records to test treatments
The proliferation of public hospitals created the first large collections of clinical records. French doctor Pierre- Charles-Alexandre Louis used early statistical analysis techniques to discredit the use of leeches in bloodletting in 1828, an approach that led to modern evidence-based medicine techniques including clinical trials and differential diagnosis techniques.
Using clinical records
to test treatments
The proliferation of public hospitals created the first significant collections of clinical records. French doctor Pierre Charles Alexandre Louis used early statistical analysis techniques to discredit the use of leeches in bloodletting in 1828, and many credit his approach as inspiration for modern evidence-based medicine techniques including clinical trials and differential diagnosis techniques.

POPULATION-LEVEL
APPROACH
While traditional medicine focused its analysis and interventions on individuals, these new disciplines centered on populations and the concept of collective risk.

POPULATION-LEVEL
APPROACH
While traditional medicine focused its analysis and interventions on individuals, these new disciplines centered their analysis and intervention on populations and the concept of collective risk.
POPULATION-LEVEL
APPROACH
While traditional medicine focused its analysis and interventions on individuals, these new disciplines centered on populations and the concept of collective risk.

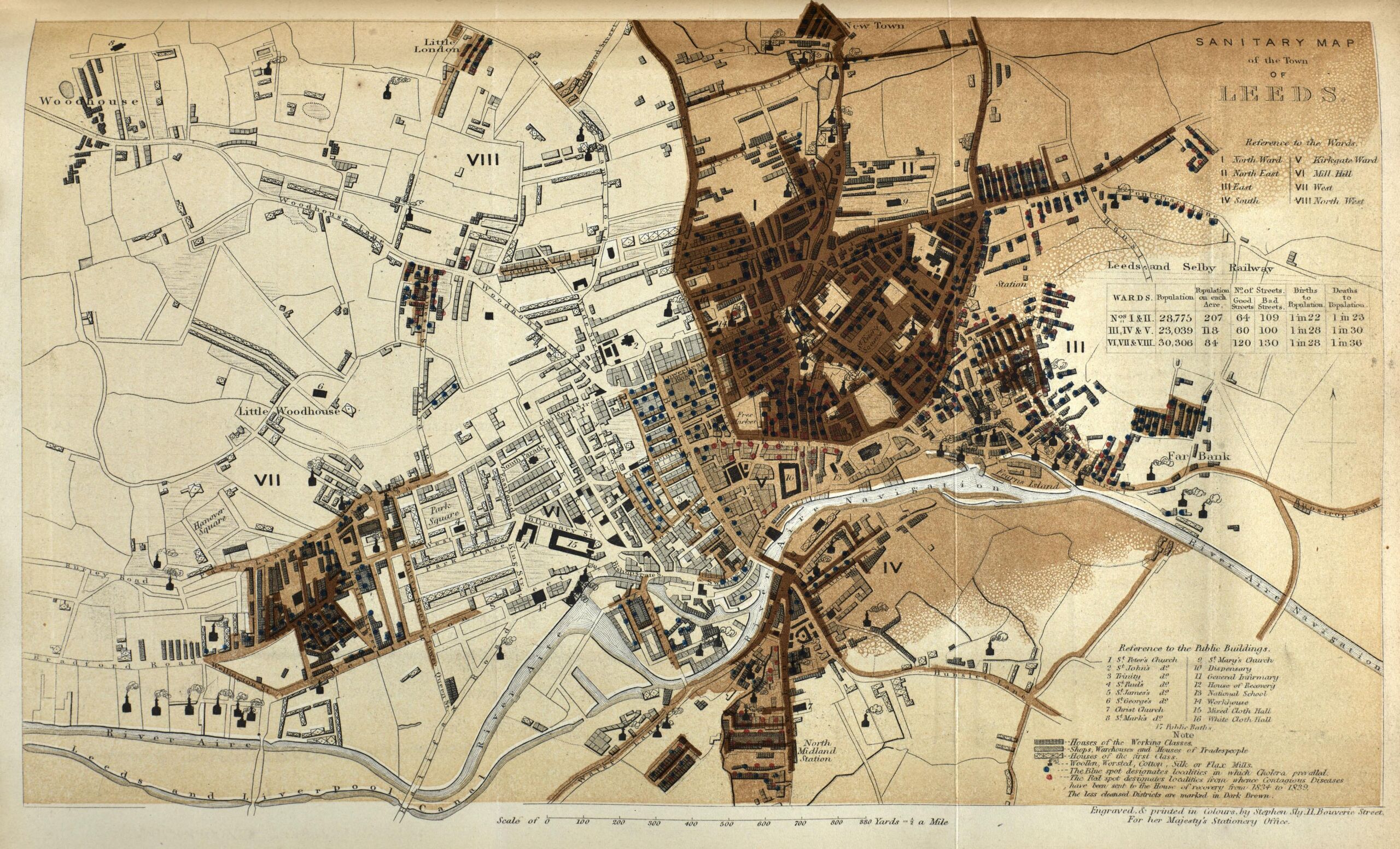
Tracking Cholera Outbreaks to Water
John Snow is often credited as the father of epidemiology for his use of city records and statistics derived from the Bills of Mortality to map cholera outbreaks in London in the mid-1800s. He found that cholera was likely transmitted through the water supply, undermining the dominant “miasma” theory of the time.
Tracking Cholera Outbreaks to Water
John Snow is often credited as the father of epidemiology for mapping cholera outbreaks in London in the mid 1800’s using data using city records and statistics derived from the Bills of Mortality. He found that cholera was likely transmitted through the water supply, undermining the dominant “miasma” theory of the time.
Tracking Cholera Outbreaks
to Water
John Snow is often credited as the father of epidemiology for mapping cholera outbreaks in London in the mid 1800’s using data using city records and statistics derived from the Bills of Mortality. He found that cholera was likely transmitted through the water supply, undermining the dominant “miasma” theory of the time.
PREVENTATIVE INTERVENTIONS &
MITIGATION STRATEGIES
Instead of focusing on the treatment of infected individuals, these new disciplines enabled physicians, scientists and public officials to develop and test preventative interventions and mitigation strategies.
PREVENTATIVE INTERVENTIONS &
MITIGATION STRATEGIES
These new disciplines opened up new opportunities to develop and test preventative interventions and mitigation strategies instead of focusing solely on post-infection interventions and treatments.

PREVENTATIVE INTERVENTIONS & MITIGATION STRATEGIES
These new disciplines opened up new opportunities to develop and test preventative interventions and mitigation strategies instead of focusing solely on post-infection interventions and treatments.

From Inoculation to Vaccination
One of the deadliest diseases known to humans, smallpox spread throughout the world in the 18th century. Communities around the world increasingly turned to science in search of methods to prevent or limit the severity of infections. In the early part of the century, physicians and advocates worked to convince a wary public of the benefits of variolation (inoculation) treatments that drastically reduced mortality, but it was the invention of a smallpox vaccine by Edward Jenner in 1796 that revolutionized the way we approach infectious diseases today.
From Inoculation to Vaccination
One of the deadliest diseases known to humans, smallpox spread throughout the world in the 18th century. To combat the threat, physicians, scientists, and communities increasingly turned to science in search of methods to preemptively treat patients to prevent or limit the severity of infections. In the early part of the century, physicians and advocates worked to convince wary publics of the benefits of variolation (inoculation) treatments that drastically reduced mortality, but it was the invention of a smallpox vaccine by Edward Jenner in 1796 that revolutionized the way we approach infectious diseases today.
From Inoculation to Vaccination
One of the deadliest diseases known to humans, smallpox spread throughout the world in the 18th century. Communities around the world increasingly turned to science in search of methods to prevent or limit the severity of infections. In the early part of the century, physicians and advocates worked to convince a wary public of the benefits of variolation (inoculation) treatments that drastically reduced mortality, but it was the invention of a smallpox vaccine by Edward Jenner in 1796 that revolutionized the way we approach infectious diseases today.
NON-MEDICAL INTERVENTIONS
Using data-driven investigation techniques, population thinking, and a newfound focus on prevention strategies, experts identified very effective non-medical interventions and mitigation strategies for infectious diseases and other causes of early mortality.
NON-MEDICAL INTERVENTIONS
Using data-driven investigation techniques, population thinking, and a newfound focus on prevention strategies, these new disciplines helped identify effective policy-based, non-medical interventions and mitigation strategies.
NON-MEDICAL INTERVENTIONS
Using data-driven investigation techniques, population thinking, and a newfound focus on prevention strategies, these new disciplines helped identify effective policy-based, non-medical interventions and mitigation strategies.
The Great Sanitary Awakening
The application of statistical analysis techniques to the spread of disease and the causes of early mortality led to “The Great Sanitary Awakening.” The 1842 “Report on the Sanitary Condition of the Labouring Population of Great Britain” used statistical evidence to disprove classist theories about life expectancy variations and led to Britain’s first Public Health Act, which included investments in improving sanitation throughout the country. As the links between overcrowding and poor sanitation were increasingly publicized, governments around the world followed suit and enhanced exploration of non-medical interventions to mitigate and prevent disease.
The Great Sanitary Awakening
The application of statistical analysis techniques to the spread of diseases and the causes of early mortality led to “The Great Sanitary Awakening.” The 1842 “Report on the Sanitary Condition of the Labouring Population of Great Britain” used statistical evidence to disprove classist theories on life expectancy variations and led to Britain’s first Public Health Act and investments in improving sanitation throughout the country. As the links between overcrowding and poor sanitation were increasingly publicized, governments around the world began to take action and it opened up a new focus on non-medical interventions to mitigate and prevent disease.
The Great Sanitary Awakening
The application of statistical analysis techniques to the spread of diseases and the causes of early mortality led to “The Great Sanitary Awakening.” The 1842 “Report on the Sanitary Condition of the Labouring Population of Great Britain” used statistical evidence to disprove classist theories on life expectancy variations and led to Britain’s first Public Health Act and investments in improving sanitation throughout the country. As the links between overcrowding and poor sanitation were increasingly publicized, governments around the world began to take action and it opened up a new focus on non-medical interventions to mitigate and prevent disease.
APPLYING PUBLIC HEALTH THINKING TO CYBERSECURITY
Adopting a public health-style perspective that embraces data-driven investigation, population thinking, and preventative approaches to shared risks would be transformative for the practice of cybersecurity. Experts could systematically test associations between risk factors and cyber threats, measure and compare the effectiveness of interventions, and adopt preventative measures that reduce both local and systemic risks to make the internet more secure and resilient for all.
In addition to reducing shared systemic risks, a Cyber Public Health approach would directly benefit enterprise security teams as well. One of the core lessons of public health models is that an individual (person or company) only has control over a small percentage of the risks they face. For example, identifying and addressing flaws in the DNS, routing, or other aspects of internet infrastructure require coordinated international action. Moreover, the data and analytical techniques developed through Cyber Public Health research will enable enterprise security teams to better evaluate existing practices, test alternatives, and better predict future threats.
APPLYING PUBLIC HEALTH THINKING TO CYBERSECURITY
Adopting a public health-style perspective that embraces data-driven investigation, population thinking, and preventative approaches to shared risks would be transformative for cybersecurity. It would allow experts to systematically test associations between risk factors and cyber threats, measure and compare the effectiveness of interventions, and adopt preventative measures that reduce both local and systemic risks to make the internet more secure and resilient for all.
In addition to reducing shared systemic risks, a Cyber Public Health approach would directly benefit enterprise security teams as well. One of the core lessons of public health models is that an individual (person or company) only has control over a small percentage of the risks they face. For example, identifying and addressing flaws in the DNS, routing or other aspects of internet infrastructure require coordinated international action. Moreover, the data and analytical techniques developed through Cyber Public Health research will enable enterprise security teams to better evaluate existing practices, test alternatives and better predict future threats.
APPLYING PUBLIC HEALTH THINKING TO CYBERSECURITY
Adopting a public health-style perspective that embraces data-driven investigation, population thinking, and preventative approaches to shared risks would be transformative for cybersecurity. It would allow experts to systematically test associations between risk factors and cyber threats, measure and compare the effectiveness of interventions, and adopt preventative measures that reduce both local and systemic risks to make the internet more secure and resilient for all.
In addition to reducing shared systemic risks, a Cyber Public Health approach would directly benefit enterprise security teams as well. One of the core lessons of public health models is that an individual (person or company) only has control over a small percentage of the risks they face. For example, identifying and addressing flaws in the DNS, routing or other aspects of internet infrastructure require coordinated international action. Moreover, the data and analytical techniques developed through Cyber Public Health research will enable enterprise security teams to better evaluate existing practices, test alternatives and better predict future threats.
THE PATH TOWARD A SCIENCE OF
CYBER PUBLIC HEALTH
Establishing a science of Cyber Public Health will require overcoming some significant challenges. The biggest challenge is data. We need to build the foundations of Cyber Public Health on vast quantities of high quality data, but we have precious little of it. Arguably, Florence Nightingale and John Smith had access to more relevant, large scale data than cybersecurity professionals today. For example, without reliable data on the number of internet-connected devices, we will struggle to answer even basic questions like, “Is malware increasing?”
CyberGreen is taking a two-pronged approach to meet this challenge. First, we are working on discrete “proof of concept” data collection and measurement projects like our “Internet Infrastructure Health Metrics Framework.” Second, we are mobilizing a global community of experts, business leaders, and policymakers to work together on proposals to unlock other critical datasets
and establish standards for the collection and reporting of key data.
The second big challenge is building the infrastructure and institutions to support a mature practice of Cyber Public Health. For example, today’s public health infrastructure includes institutions at every level of government, international NGOs, academic institutions, and private organizations that play a role.
This is another area where coordination and collaboration among businesses, NGO’s, academic institutions, and governments will be critical to navigating a path forward. The challenges are significant, but the opportunities are immense. Please join our community and help us make Cyber Public Health a critical part of making the internet safe and resilient for everyone.
THE PATH TOWARD A SCIENCE OF
CYBER PUBLIC HEALTH
Establishing a science of Cyber Public Health will require overcoming some significant challenges. The biggest challenge is data. We need to build the foundations of Cyber Public Health on vast quantities of high quality data, but we have precious little of it. Arguably, Florence Nightingale and John Smith had access to more relevant, large scale data than cybersecurity professionals today. For example, without reliable data on the number of internet-connected devices, we will struggle to answer even basic questions like, “Is malware increasing?”
CyberGreen is taking a two-pronged approach to meet this challenge. First, we are working on discrete “proof of concept” data collection and measurement projects like our “Internet Infrastructure Health Metrics Framework.” Second, we are mobilizing a global community of experts, business leaders, and policymakers to work together on proposals to unlock other critical datasets
and establish standards for the collection and reporting of key data.
The second big challenge is building the infrastructure and institutions to support a mature practice of Cyber Public Health. For example, today’s public health infrastructure includes institutions at every level of government, international NGOs, academic institutions, and private organizations that play a role.
This is another area where coordination and collaboration among businesses, NGO’s, academic institutions, and governments will be critical to navigating a path forward. The challenges are significant, but the opportunities are immense. Please join our community and help us make Cyber Public Health a critical part of making the internet safe and resilient for everyone.
THE PATH TOWARD A SCIENCE OF CYBER PUBLIC HEALTH
Establishing a science of Cyber Public Health will require overcoming some significant challenges. The biggest challenge is data. We need to build the foundations of Cyber Public Health on vast quantities of high quality data, but we have precious little of it. Arguably, Florence Nightingale and John Smith had access to more relevant, large scale data than cybersecurity professionals today. For example, without reliable data on the number of internet-connected devices, we will struggle to answer even basic questions like, “Is malware increasing?”
CyberGreen is taking a two-pronged approach to meet this challenge. First, we are working on discrete “proof of concept” data collection and measurement projects like our “Internet Infrastructure Health Metrics Framework.” Second, we are mobilizing a global community of experts, business leaders, and policymakers to work together on proposals to unlock other critical datasets
and establish standards for the collection and reporting of key data.
The second big challenge is building the infrastructure and institutions to support a mature practice of Cyber Public Health. For example, today’s public health infrastructure includes institutions at every level of government, international NGOs, academic institutions, and private organizations that play a role.
This is another area where coordination and collaboration among businesses, NGO’s, academic institutions, and governments will be critical to navigating a path forward. The challenges are significant, but the opportunities are immense. Please join our community and help us make Cyber Public Health a critical part of making the internet safe and resilient for everyone.
